Telemore AI LLC
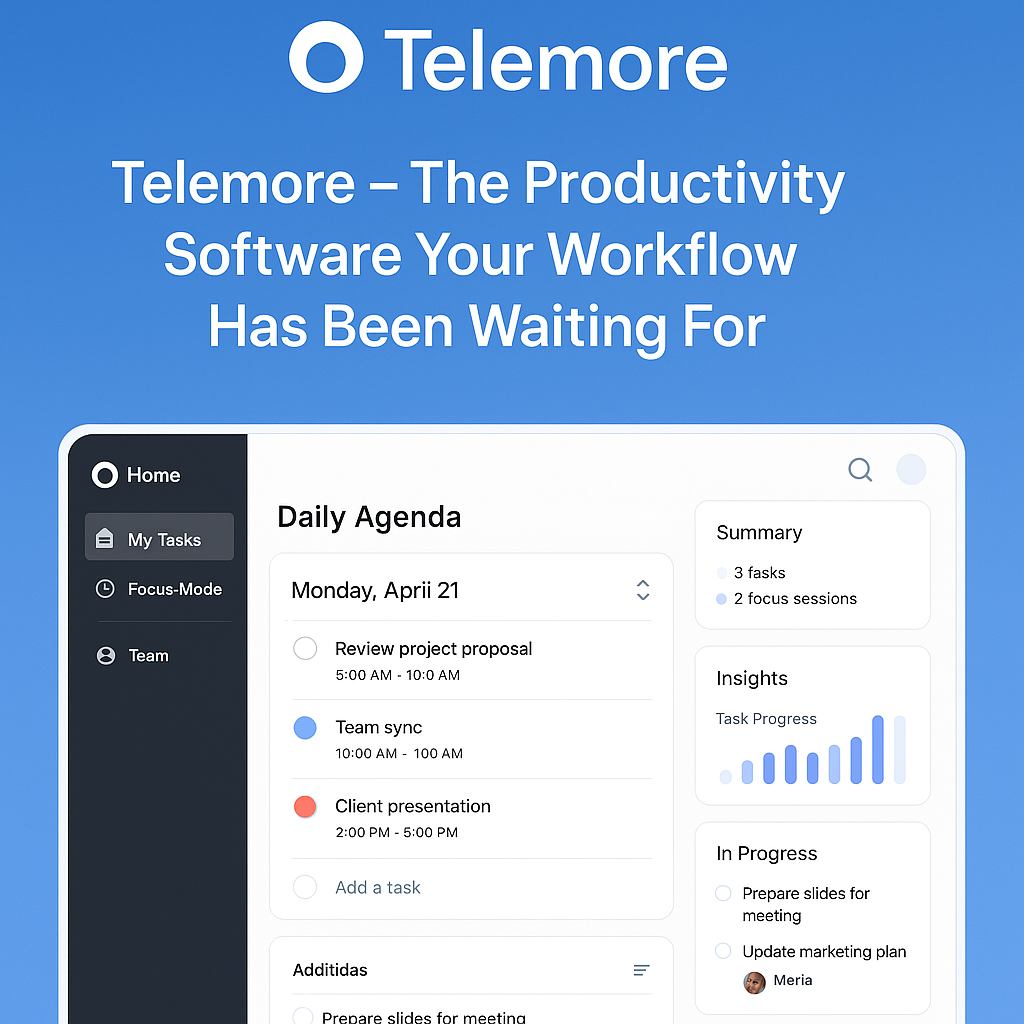
Freelancers and managers alike benefit from screenshot monitoring software. Track billable hours, showcase proof of work.
2 months ago
Telemore – The Productivity Software Your Workflow Has Been Waiting For
We’ve all tried countless to-do lists, color-coded calendars, browser extensions, and the latest “Top 10 Productivity Hacks” from YouTube. But despite our best efforts, the chaos of modern work persists. Deadlines get missed, priorities shift constantly, and tasks somehow fall through the cracks.
https://telemore.ai/produc...
We’ve all tried countless to-do lists, color-coded calendars, browser extensions, and the latest “Top 10 Productivity Hacks” from YouTube. But despite our best efforts, the chaos of modern work persists. Deadlines get missed, priorities shift constantly, and tasks somehow fall through the cracks.
https://telemore.ai/produc...
1 month ago
Data Masking Market Demand, Data Masking Market Growth, Data Masking market, Data Masking Market Trend, Data Masking Market Research Report, Data Masking Market Size, Data Masking Market Share, Data Masking Market Price
Global Data Masking Market Projected to Reach USD 1.68 Billion by 2030, Driven by Rising Cybersecurity Demands and Regulatory Compliance
The global Data Masking Market Size is poised for significant growth, projected to expand from USD 0.72 billion in 2023 to USD 1.68 billion by 2030, registering a robust CAGR of 12.85% during the forecast period. This surge is fueled by increasing cyber threats, stringent data protection regulations, and the need for secure data management across various industries.
Ask for Sample to Know US Tariff Impacts on Market @https://www.maximizemarket...
Market Estimation & Definition
Data masking is a data security technique that involves transforming sensitive information into a non-sensitive version, ensuring that unauthorized users cannot access the original data. This method is widely used in commercial applications to protect personal identities and sensitive information within corporate organizations. By converting important, structured, and organized data into complex replicas, data masking serves as a model for training and testing applications without compromising actual data.
Market Growth Drivers & Opportunities
1. Escalating Cybersecurity Threats: The rise in cyber-attacks, particularly from nation-state hackers, has heightened the need for robust data protection measures. Countries like the United States have faced sophisticated cyber risks from adversaries such as Russia and China, leading to significant data breaches. These threats underscore the importance of data masking in safeguarding sensitive information.
2. Regulatory Compliance: Stringent data protection regulations, including GDPR in Europe and CCPA in California, mandate organizations to implement measures that protect personal data. Data masking helps businesses comply with these regulations by ensuring that sensitive information is not exposed during processes like software testing and data analysis.
3. Adoption of Cloud Technologies: The shift towards cloud computing has increased the need for data masking solutions that can secure data in dynamic and distributed environments. As organizations migrate to cloud platforms, data masking ensures that sensitive information remains protected across various cloud services.
4. Demand for Secure Data Management: Industries such as finance, healthcare, and retail require secure data management practices to protect customer information. Data masking enables these sectors to handle data securely, reducing the risk of data breaches and maintaining customer trust.
Request a Sample of the US Tariff Impact Analysis Report:https://www.maximizemarket...
Segmentation Analysis
The data masking market is segmented based on type, component, business function, organization size, deployment type, industry vertical, and region.
By Type:
Static Data Masking: Involves creating a sanitized copy of a database where sensitive data is replaced with fictitious data. This method is commonly used in non-production environments like testing and development.
Dynamic Data Masking: Applies masking rules in real-time as users access data, ensuring that sensitive information is not exposed during live operations. This approach is beneficial for production environments where data privacy is paramount.
By Component:
Software: Includes standalone data masking tools and integrated solutions that provide functionalities like data discovery, classification, and masking.
Services: Encompasses professional services such as consulting, implementation, and support, helping organizations deploy and manage data masking solutions effectively.
By Business Function:
Web Performance Optimization: Ensures that sensitive data is protected during website performance testing and optimization processes.
Media Delivery: Protects personal data in media content distribution, ensuring compliance with privacy regulations.
Finance: Secures financial data during processing and analysis, mitigating risks **** ociated with data breaches.
Operations: Safeguards operational data, maintaining the integrity and confidentiality of business processes.
Marketing and Sales: Protects customer data used in marketing campaigns and sales strategies, ensuring compliance with data protection laws.
Human Resources: Secures employee information during HR processes like recruitment and performance evaluations.
Legal: Ensures that sensitive legal documents and communications are protected from unauthorized access.
Others: Includes additional business functions where data masking is applied to protect sensitive information.
By Organization Size:
Small and Medium Enterprises (SMEs): Adopt data masking solutions to protect sensitive data without the need for extensive IT infrastructure.
Large Enterprises: Implement comprehensive data masking strategies to secure vast amounts of sensitive information across various departments.
By Deployment Type:
On-Premises: Organizations deploy data masking solutions within their own infrastructure, providing full control over data security.
Cloud-Based: Data masking solutions are offered as cloud services, providing scalability and flexibility for organizations leveraging cloud environments.
By Industry Vertical:
BFSI (Banking, Financial Services, and Insurance): Utilizes data masking to protect financial data and comply with regulatory requirements.
Healthcare: Applies data masking to secure patient information and adhere to health data protection laws.
Retail and E-commerce: Protects customer data during transactions and marketing activities.
IT and Telecom: Implements data masking to secure sensitive information in IT services and telecommunications.
Government: Uses data masking to protect citizen data and maintain national security.
Others: Includes various other sectors where data masking is essential for data protection.
Country-Level Analysis
United States:
The United States is a significant player in the data masking market, with a market size estimated at USD 210.2 million in 2024. The country's advanced IT infrastructure, coupled with stringent data protection regulations, drives the adoption of data masking solutions. High-profile cyber-attacks have further emphasized the need for robust data security measures.
Germany:
Germany is expected to experience substantial growth in the data masking market, with a projected CAGR of approximately 9.1% from 2024 to 2030. The country's focus on data privacy and compliance with the General Data Protection Regulation (GDPR) has led to increased investment in data masking technologies. Industries such as manufacturing and finance are key adopters of these solutions.
For deeper market insights, peruse the summary of the research report:https://www.maximizemarket...
Competitor Analysis
The data masking market is characterized by the presence of several key players who offer a range of solutions and services:
IBM Corporation: Offers comprehensive data masking solutions integrated with its broader data security portfolio.
Oracle Corporation: Provides data masking features within its database management systems, catering to various industries.
Informatica: Delivers data masking tools that focus on data integration and cloud data management.
Delphix Corp.: Specializes in data virtualization and masking solutions that accelerate application development.
Mentis: Offers data security solutions with a focus on sensitive data discovery and masking.
Micro Focus: Provides data masking as part of its broader data protection and privacy offerings.
Compuware Corporation: Delivers data masking tools aimed at mainframe application development and testing.
These companies are investing in research and development to enhance their data masking capabilities, focusing on automation, scalability, and integration with other data security tools.
Reasons to Buy
Access data-driven insights to inform investment and development strategies
Understand competitive positioning across regions
Discover emerging opportunities in key application segments
Stay ahead with accurate forecasts and trend analysis
Key Highlights:
Historical Market Data (2018-2023)
Forecasts by Segment, Region, and Industry Application (2024-2030)
SWOT Analysis, Value Chain Insights, and Growth Drivers
Legal Aspects by Region and Emerging Opportunities
Top Questions Answered:
What are the key growth drivers and trends in the market?
Who are the major players, and how do they maintain a competitive edge?
What new applications are poised to revolutionize the Data Masking industry?
How will the market grow in the coming years, and at what rate?
Latest cutting-edge research from Maximize Market Research is now trending:
Global Clinical Communication & Collaboration Market https://www.maximizemarket...
Global Speech-to-Text API Market https://www.maximizemarket...
Global Disk Based Data Fabric Market https://www.maximizemarket...
About Maximize Market Research:
Maximize Market Research is a multifaceted market research and consulting company with professionals from several industries. Some of the industries we cover include medical devices, pharmaceutical manufacturers, science and engineering, electronic components, industrial equipment, technology and communication, cars and automobiles, chemical
Global Data Masking Market Projected to Reach USD 1.68 Billion by 2030, Driven by Rising Cybersecurity Demands and Regulatory Compliance
The global Data Masking Market Size is poised for significant growth, projected to expand from USD 0.72 billion in 2023 to USD 1.68 billion by 2030, registering a robust CAGR of 12.85% during the forecast period. This surge is fueled by increasing cyber threats, stringent data protection regulations, and the need for secure data management across various industries.
Ask for Sample to Know US Tariff Impacts on Market @https://www.maximizemarket...
Market Estimation & Definition
Data masking is a data security technique that involves transforming sensitive information into a non-sensitive version, ensuring that unauthorized users cannot access the original data. This method is widely used in commercial applications to protect personal identities and sensitive information within corporate organizations. By converting important, structured, and organized data into complex replicas, data masking serves as a model for training and testing applications without compromising actual data.
Market Growth Drivers & Opportunities
1. Escalating Cybersecurity Threats: The rise in cyber-attacks, particularly from nation-state hackers, has heightened the need for robust data protection measures. Countries like the United States have faced sophisticated cyber risks from adversaries such as Russia and China, leading to significant data breaches. These threats underscore the importance of data masking in safeguarding sensitive information.
2. Regulatory Compliance: Stringent data protection regulations, including GDPR in Europe and CCPA in California, mandate organizations to implement measures that protect personal data. Data masking helps businesses comply with these regulations by ensuring that sensitive information is not exposed during processes like software testing and data analysis.
3. Adoption of Cloud Technologies: The shift towards cloud computing has increased the need for data masking solutions that can secure data in dynamic and distributed environments. As organizations migrate to cloud platforms, data masking ensures that sensitive information remains protected across various cloud services.
4. Demand for Secure Data Management: Industries such as finance, healthcare, and retail require secure data management practices to protect customer information. Data masking enables these sectors to handle data securely, reducing the risk of data breaches and maintaining customer trust.
Request a Sample of the US Tariff Impact Analysis Report:https://www.maximizemarket...
Segmentation Analysis
The data masking market is segmented based on type, component, business function, organization size, deployment type, industry vertical, and region.
By Type:
Static Data Masking: Involves creating a sanitized copy of a database where sensitive data is replaced with fictitious data. This method is commonly used in non-production environments like testing and development.
Dynamic Data Masking: Applies masking rules in real-time as users access data, ensuring that sensitive information is not exposed during live operations. This approach is beneficial for production environments where data privacy is paramount.
By Component:
Software: Includes standalone data masking tools and integrated solutions that provide functionalities like data discovery, classification, and masking.
Services: Encompasses professional services such as consulting, implementation, and support, helping organizations deploy and manage data masking solutions effectively.
By Business Function:
Web Performance Optimization: Ensures that sensitive data is protected during website performance testing and optimization processes.
Media Delivery: Protects personal data in media content distribution, ensuring compliance with privacy regulations.
Finance: Secures financial data during processing and analysis, mitigating risks **** ociated with data breaches.
Operations: Safeguards operational data, maintaining the integrity and confidentiality of business processes.
Marketing and Sales: Protects customer data used in marketing campaigns and sales strategies, ensuring compliance with data protection laws.
Human Resources: Secures employee information during HR processes like recruitment and performance evaluations.
Legal: Ensures that sensitive legal documents and communications are protected from unauthorized access.
Others: Includes additional business functions where data masking is applied to protect sensitive information.
By Organization Size:
Small and Medium Enterprises (SMEs): Adopt data masking solutions to protect sensitive data without the need for extensive IT infrastructure.
Large Enterprises: Implement comprehensive data masking strategies to secure vast amounts of sensitive information across various departments.
By Deployment Type:
On-Premises: Organizations deploy data masking solutions within their own infrastructure, providing full control over data security.
Cloud-Based: Data masking solutions are offered as cloud services, providing scalability and flexibility for organizations leveraging cloud environments.
By Industry Vertical:
BFSI (Banking, Financial Services, and Insurance): Utilizes data masking to protect financial data and comply with regulatory requirements.
Healthcare: Applies data masking to secure patient information and adhere to health data protection laws.
Retail and E-commerce: Protects customer data during transactions and marketing activities.
IT and Telecom: Implements data masking to secure sensitive information in IT services and telecommunications.
Government: Uses data masking to protect citizen data and maintain national security.
Others: Includes various other sectors where data masking is essential for data protection.
Country-Level Analysis
United States:
The United States is a significant player in the data masking market, with a market size estimated at USD 210.2 million in 2024. The country's advanced IT infrastructure, coupled with stringent data protection regulations, drives the adoption of data masking solutions. High-profile cyber-attacks have further emphasized the need for robust data security measures.
Germany:
Germany is expected to experience substantial growth in the data masking market, with a projected CAGR of approximately 9.1% from 2024 to 2030. The country's focus on data privacy and compliance with the General Data Protection Regulation (GDPR) has led to increased investment in data masking technologies. Industries such as manufacturing and finance are key adopters of these solutions.
For deeper market insights, peruse the summary of the research report:https://www.maximizemarket...
Competitor Analysis
The data masking market is characterized by the presence of several key players who offer a range of solutions and services:
IBM Corporation: Offers comprehensive data masking solutions integrated with its broader data security portfolio.
Oracle Corporation: Provides data masking features within its database management systems, catering to various industries.
Informatica: Delivers data masking tools that focus on data integration and cloud data management.
Delphix Corp.: Specializes in data virtualization and masking solutions that accelerate application development.
Mentis: Offers data security solutions with a focus on sensitive data discovery and masking.
Micro Focus: Provides data masking as part of its broader data protection and privacy offerings.
Compuware Corporation: Delivers data masking tools aimed at mainframe application development and testing.
These companies are investing in research and development to enhance their data masking capabilities, focusing on automation, scalability, and integration with other data security tools.
Reasons to Buy
Access data-driven insights to inform investment and development strategies
Understand competitive positioning across regions
Discover emerging opportunities in key application segments
Stay ahead with accurate forecasts and trend analysis
Key Highlights:
Historical Market Data (2018-2023)
Forecasts by Segment, Region, and Industry Application (2024-2030)
SWOT Analysis, Value Chain Insights, and Growth Drivers
Legal Aspects by Region and Emerging Opportunities
Top Questions Answered:
What are the key growth drivers and trends in the market?
Who are the major players, and how do they maintain a competitive edge?
What new applications are poised to revolutionize the Data Masking industry?
How will the market grow in the coming years, and at what rate?
Latest cutting-edge research from Maximize Market Research is now trending:
Global Clinical Communication & Collaboration Market https://www.maximizemarket...
Global Speech-to-Text API Market https://www.maximizemarket...
Global Disk Based Data Fabric Market https://www.maximizemarket...
About Maximize Market Research:
Maximize Market Research is a multifaceted market research and consulting company with professionals from several industries. Some of the industries we cover include medical devices, pharmaceutical manufacturers, science and engineering, electronic components, industrial equipment, technology and communication, cars and automobiles, chemical
Aditya Gaurav
Visionary Founder | Global Award-Winning Innovator #entrepreneur #speaker #leader #founder #student #mentor #career
1 yr. ago
How games hack your brain and hook you 😲 (Read caption) ⬇️
Rewards & Reinforcement: Getting rewards makes
your brain want to keep playing.
Flow State: Being involved deeply makes
your brain lose track of time.
Cognitive Load Theory: Games are designed
to be just complex enough to be interesting
but not too hard.
Chunking: Information & tasks in game are
broken down into small, manageable parts.
Feedback Loops: You get constant feedback,
which motivates you to improve.
Visual and Spatial Perception: Games are
visually appealing to make you feel immersed.
Problem-Solving & Strategy: Games challenge
you to think and plan, keeping you hooked.
Intermittent Rewards: Rewards are given
out at random intervals to keep the
excitement alive.
Achievement & Progression: Players feel
a sense of accomplishment as they progress.
Player Autonomy & Agency: You get the
freedom to make choices that affect the game.
Social Interaction: Games encourage you to
interact with others, creating a community feeling.
Addressing Feedback: Games evolve based on
players suggestions, making you feel heard.
Follow me adityagauravkc for more.
Like and share with friends.
#[1718] #[1719] #[1720] #[1721] #[1722] #[1723] #[1724] #[1725] #[1726] #[1727] #[1728] #[1729] #[1730] #[1731]
Rewards & Reinforcement: Getting rewards makes
your brain want to keep playing.
Flow State: Being involved deeply makes
your brain lose track of time.
Cognitive Load Theory: Games are designed
to be just complex enough to be interesting
but not too hard.
Chunking: Information & tasks in game are
broken down into small, manageable parts.
Feedback Loops: You get constant feedback,
which motivates you to improve.
Visual and Spatial Perception: Games are
visually appealing to make you feel immersed.
Problem-Solving & Strategy: Games challenge
you to think and plan, keeping you hooked.
Intermittent Rewards: Rewards are given
out at random intervals to keep the
excitement alive.
Achievement & Progression: Players feel
a sense of accomplishment as they progress.
Player Autonomy & Agency: You get the
freedom to make choices that affect the game.
Social Interaction: Games encourage you to
interact with others, creating a community feeling.
Addressing Feedback: Games evolve based on
players suggestions, making you feel heard.
Follow me adityagauravkc for more.
Like and share with friends.
#[1718] #[1719] #[1720] #[1721] #[1722] #[1723] #[1724] #[1725] #[1726] #[1727] #[1728] #[1729] #[1730] #[1731]
Aditya Gaurav
Visionary Founder | Global Award-Winning Innovator #entrepreneur #speaker #leader #founder #student #mentor #career
1 yr. ago
Highest paying, Low competition careers to pursue after high school ⬇️
Cybersecurity/Ethical hacker
Biotechnology,
Prosthetist & Orthotist
Green energy (solar, wind, water) engineer
Taxidermist,
Drone pilots,
UX designers
Epidemiologist,
Molecular biologist
Biostatistician,
Genetic counselor
Nuclear medicine technologist
Healthcare consultant,
Cloud engineer
Data privacy officer
Sustainability consultant
Forensic accountant,
Robotic engineer
Geospatial information scientist
Bioinformatics scientist,
Actuarial analyst
Hydrologist,
Astronomer
Atmospheric scientist,
Pharmacist
Medical science Liaison
Cryptographer,
Petrol Engineer
Photonics engineer,
Magnet engineer
PC/Console Game Developer
Pediatrician,
Physician assistant
Marine biologist,
Food scientist
Urban planner,
Data scientist
Information security analyst
AI specialist,
Compensation manager.
Note that salaries & competition may vary based on your location, check accordingly.
Follow me @[1] for more.
Like & Share with all friends in school.
#[1816] #[1755] #[1817] #[1818] #[29] #[1767] #[1819] #[283] #[1423] #[1820] #[285] #[1821] #[1822] #[1823] #[1824] #[1756] #[1757] #[1825] #[1826] #[1827] #[1828] #[277] #[695] #[1829] #[1830] #[1831] #[1832] #[1833]
Cybersecurity/Ethical hacker
Biotechnology,
Prosthetist & Orthotist
Green energy (solar, wind, water) engineer
Taxidermist,
Drone pilots,
UX designers
Epidemiologist,
Molecular biologist
Biostatistician,
Genetic counselor
Nuclear medicine technologist
Healthcare consultant,
Cloud engineer
Data privacy officer
Sustainability consultant
Forensic accountant,
Robotic engineer
Geospatial information scientist
Bioinformatics scientist,
Actuarial analyst
Hydrologist,
Astronomer
Atmospheric scientist,
Pharmacist
Medical science Liaison
Cryptographer,
Petrol Engineer
Photonics engineer,
Magnet engineer
PC/Console Game Developer
Pediatrician,
Physician assistant
Marine biologist,
Food scientist
Urban planner,
Data scientist
Information security analyst
AI specialist,
Compensation manager.
Note that salaries & competition may vary based on your location, check accordingly.
Follow me @[1] for more.
Like & Share with all friends in school.
#[1816] #[1755] #[1817] #[1818] #[29] #[1767] #[1819] #[283] #[1423] #[1820] #[285] #[1821] #[1822] #[1823] #[1824] #[1756] #[1757] #[1825] #[1826] #[1827] #[1828] #[277] #[695] #[1829] #[1830] #[1831] #[1832] #[1833]
Novella Kitchens
Novella Kitchens in Gurgaon, we make luxury modular kitchens and wardrobes that look really fancy!
3 months ago
Looking to make the most of your small bedroom? Our latest blog, "Small Bedroom Ideas 2025: Space & Style," is packed with smart tips to maximize space without compromising on design. Discover clever storage hacks, layout ideas, and stylish solutions. Visit us at Novella Kitchens for space-saving interior solutions!
Read More: https://novellakitchens.co...
#NovellaKitchens #SmallBedroomIdeas #SpaceSavingDesign #2025HomeTrends #SmartInteriors #BedroomMakeover #CompactLiving #InteriorDesign #StylishSpaces #HomeInspiration
Read More: https://novellakitchens.co...
#NovellaKitchens #SmallBedroomIdeas #SpaceSavingDesign #2025HomeTrends #SmartInteriors #BedroomMakeover #CompactLiving #InteriorDesign #StylishSpaces #HomeInspiration
Aditya Gaurav
Visionary Founder | Global Award-Winning Innovator #entrepreneur #speaker #leader #founder #student #mentor #career
10 months ago
Your phone knows you better than yourself? ⬇️
Like and Share with friends and family. Follow me and Read below.
Devices, applications and sites, all are filled with analytical tools that work in the background to collect your data such as Date of birth, Name, Nickname, username, IP addresses you visited, your social media accounts, your device's model, how much battery it usually has, resolution of your device, your preferred language, your preferred day or night mode, your visit time, how many clicks you did and on what elements, where you stopped to stare, which page made you close the app/site, which app referred you to current app, what do you search and when, your state, city, your home and who you live with.
And thousands of other critically important data points are collected from your personal life.
The outcome? This data can now be used to know what emotion are you going through, when women will have menstrual cycle, when and why do you go out, what you will do today, what do you think, why you visited a person, your psychology, your relatives, your family and friends, who you interact with and why, which product you need right now, which problem your are facing rn, what are your habits and other uncountable things, depends upon how an organization want to use it for selling you stuff.
To save yourself from this, use Knowasiak social network, it doesn't stores your private data and we don't use it internally to do any calculations to sell you stuff. On Knowasiak you own your own data, without anyone sneaking in your private life.
Follow me @adityagaurav for more.
Like and Share with your Friends.
#hack #hacked #private #data #personaldata #location #ip #life #analytics #tracking #findout #saveyourself #socialmedia #networking #internet #friends #school #privacy #privacymatters #knowasiak
Like and Share with friends and family. Follow me and Read below.
Devices, applications and sites, all are filled with analytical tools that work in the background to collect your data such as Date of birth, Name, Nickname, username, IP addresses you visited, your social media accounts, your device's model, how much battery it usually has, resolution of your device, your preferred language, your preferred day or night mode, your visit time, how many clicks you did and on what elements, where you stopped to stare, which page made you close the app/site, which app referred you to current app, what do you search and when, your state, city, your home and who you live with.
And thousands of other critically important data points are collected from your personal life.
The outcome? This data can now be used to know what emotion are you going through, when women will have menstrual cycle, when and why do you go out, what you will do today, what do you think, why you visited a person, your psychology, your relatives, your family and friends, who you interact with and why, which product you need right now, which problem your are facing rn, what are your habits and other uncountable things, depends upon how an organization want to use it for selling you stuff.
To save yourself from this, use Knowasiak social network, it doesn't stores your private data and we don't use it internally to do any calculations to sell you stuff. On Knowasiak you own your own data, without anyone sneaking in your private life.
Follow me @adityagaurav for more.
Like and Share with your Friends.
#hack #hacked #private #data #personaldata #location #ip #life #analytics #tracking #findout #saveyourself #socialmedia #networking #internet #friends #school #privacy #privacymatters #knowasiak
Universal Crypto Signals
# Best crypto trading signals on telegram
20 days ago
The Future of Crypto Custody: What Every Provider Needs to Offer
https://www.universalcrypt...
As cryptocurrency adoption accelerates in 2025, one thing is becoming crystal clear: crypto custody is no longer just about secure storage—it’s about trust, transparency, and user empowerment.
Whether you’re an exchange, **** et manager, or retail-focused crypto platform, offering advanced custody services is essential. In this blog, we’ll break down the emerging trends in crypto custody and what today’s providers must deliver to stay ahead of the curve.
Why Custody Matters More Than Ever
With billions of dollars in digital **** ets now under management globally, custody has evolved from a backend function to a core offering. Hacks, mismanagement, and regulatory fines have shown the consequences of inadequate infrastructure.
Users today demand:
Absolute security for private keysInstant access to their **** etsInsurance-backed coverageRegulatory-grade compliance
As institutional investors enter the space, these standards are no longer negotiable—they are requirements.
The Key Elements of Modern Crypto CustodyMulti-Sig and MPC Security Protocols
Advanced platforms now rely on multi-signature wallets and multi-party computation (MPC) to eliminate single points of failure and decentralize key management.
Cold, Warm, and Hot Storage Tiers
Providers must offer tiered storage solutions with varying access levels based on **** et usage—balancing security and liquidity.
Regulatory Alignment
Global compliance standards such as SOC 2, ISO 27001, and jurisdiction-specific custody licenses are now expected by both users and regulators.
Insurance ProtectionLeading custody providers are securing third-party insurance coverage to protect against theft, loss, or breaches.
Integrated DeFi and Staking AccessThe future of custody isn’t just about storage—it includes earning opportunities like staking, lending, and real-time DeFi access from secure environments.Providers Setting the Standard
One standout example of next-gen custody evolution is Universal Crypto Signals. Their platform integrates trading signals with advanced custody insights and secure infrastructure to support traders and providers seeking more than just transactional tools.
They’re helping redefine what smart crypto management looks like by offering features such as:
Secure access to high-quality crypto signalsReal-time market analytics and trackingEnhanced account protection measures
Such platforms demonstrate how providers must blend usability, security, and performance to attract and retain users in 2025.
What Providers Must Offer Going Forward
To remain competitive, custody providers should:
Enable instant **** et mobility while preserving security.Offer full transparency on custody mechanisms.Support cross-chain **** et management and token standard compatibility (ERC-20, BEP-20, etc.).Provide customer-first onboarding with intuitive UIs and educational support.Stay audit-ready with open reporting and real-time monitoring.Final Thoughts
The future of crypto custody is dynamic, user-centric, and heavily regulated. As the digital **** et space matures, service providers must move from traditional cold storage toward full-stack custody ecosystems.
Platforms like Universal Crypto Signals showcase how combining functionality, security, and trust is no longer optional—it’s the new benchmark.
If you’re a crypto platform or provider, now is the time to invest in custody innovation. Your users—and regulators—are watching.
#Universal_Crypto_Signals , #custody_innovation , #secure_crypto_storage , #crypto_asset_management , #usercentric_custody , #crypto_custody , #digital_asset_security , #multisig_wallets , #MPC_crypto_security , #cold_storage , #hot_wallet_security , #crypto_compliance
https://www.universalcrypt...
As cryptocurrency adoption accelerates in 2025, one thing is becoming crystal clear: crypto custody is no longer just about secure storage—it’s about trust, transparency, and user empowerment.
Whether you’re an exchange, **** et manager, or retail-focused crypto platform, offering advanced custody services is essential. In this blog, we’ll break down the emerging trends in crypto custody and what today’s providers must deliver to stay ahead of the curve.
Why Custody Matters More Than Ever
With billions of dollars in digital **** ets now under management globally, custody has evolved from a backend function to a core offering. Hacks, mismanagement, and regulatory fines have shown the consequences of inadequate infrastructure.
Users today demand:
Absolute security for private keysInstant access to their **** etsInsurance-backed coverageRegulatory-grade compliance
As institutional investors enter the space, these standards are no longer negotiable—they are requirements.
The Key Elements of Modern Crypto CustodyMulti-Sig and MPC Security Protocols
Advanced platforms now rely on multi-signature wallets and multi-party computation (MPC) to eliminate single points of failure and decentralize key management.
Cold, Warm, and Hot Storage Tiers
Providers must offer tiered storage solutions with varying access levels based on **** et usage—balancing security and liquidity.
Regulatory Alignment
Global compliance standards such as SOC 2, ISO 27001, and jurisdiction-specific custody licenses are now expected by both users and regulators.
Insurance ProtectionLeading custody providers are securing third-party insurance coverage to protect against theft, loss, or breaches.
Integrated DeFi and Staking AccessThe future of custody isn’t just about storage—it includes earning opportunities like staking, lending, and real-time DeFi access from secure environments.Providers Setting the Standard
One standout example of next-gen custody evolution is Universal Crypto Signals. Their platform integrates trading signals with advanced custody insights and secure infrastructure to support traders and providers seeking more than just transactional tools.
They’re helping redefine what smart crypto management looks like by offering features such as:
Secure access to high-quality crypto signalsReal-time market analytics and trackingEnhanced account protection measures
Such platforms demonstrate how providers must blend usability, security, and performance to attract and retain users in 2025.
What Providers Must Offer Going Forward
To remain competitive, custody providers should:
Enable instant **** et mobility while preserving security.Offer full transparency on custody mechanisms.Support cross-chain **** et management and token standard compatibility (ERC-20, BEP-20, etc.).Provide customer-first onboarding with intuitive UIs and educational support.Stay audit-ready with open reporting and real-time monitoring.Final Thoughts
The future of crypto custody is dynamic, user-centric, and heavily regulated. As the digital **** et space matures, service providers must move from traditional cold storage toward full-stack custody ecosystems.
Platforms like Universal Crypto Signals showcase how combining functionality, security, and trust is no longer optional—it’s the new benchmark.
If you’re a crypto platform or provider, now is the time to invest in custody innovation. Your users—and regulators—are watching.
#Universal_Crypto_Signals , #custody_innovation , #secure_crypto_storage , #crypto_asset_management , #usercentric_custody , #crypto_custody , #digital_asset_security , #multisig_wallets , #MPC_crypto_security , #cold_storage , #hot_wallet_security , #crypto_compliance
Sponsored by
Aditya Gaurav
7 months ago
Maximize Your Brand's Exposure — Instantly!
Join thousands of successful advertisers who trust Knowasiak to amplify their visibility.
Reach 10,000+ verified users every week
Showcase your business to a highly engaged, global audience
Start advertising for just $1
Your ad. Our platform. Unlimited potential.